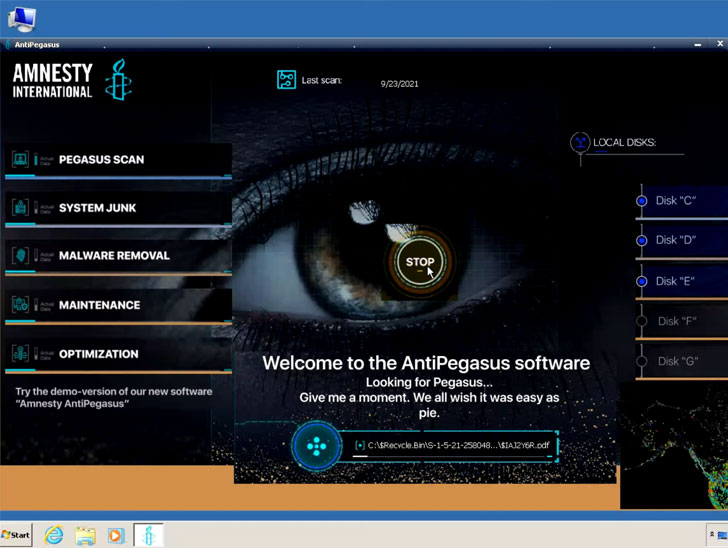
In yet another indicator of how hacking groups are quick to capitalize on world events and improvise their attack campaigns for maximum impact, threat actors have been discovered impersonating Amnesty International to distribute malware that purports to be security software designed to safeguard against NSO Group’s Pegasus surveillanceware.
“Adversaries have set up a phony website that looks like Amnesty International’s — a human rights-focused non-governmental organization — and points to a promised antivirus tool to protect against the NSO Group’s Pegasus tool,” Cisco Talos researchers said. “However, the download actually installs the little-known Sarwent malware.”
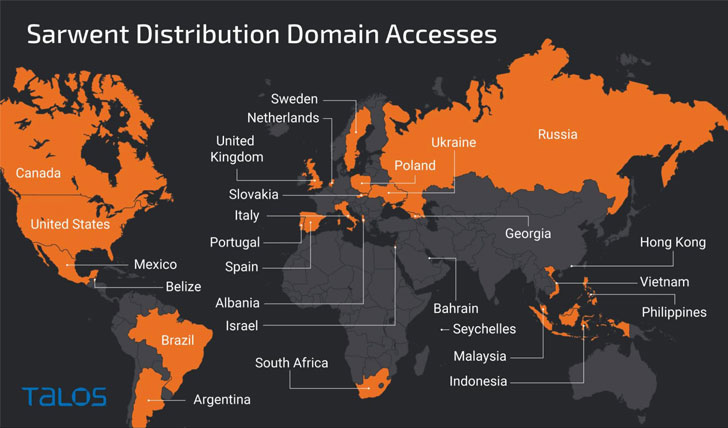
The countries most affected by the campaign include the U.K., the U.S., Russia, India, Ukraine, Czech Republic, Romania, and Colombia. While it’s unclear as to how the victims are lured into visiting the fake Amnesty International website, the cybersecurity firm surmised the attacks could be aimed at users who may be specifically searching for protection against this threat.
The development comes on the heels of an explosive investigation in July 2021 that revealed widespread abuse of the Israeli company’s Pegasus “military-grade spyware” to facilitate human rights violations by surveilling heads of state, activists, journalists, and lawyers around the world. The NGO has since also released a Mobile Verification Toolkit (MVT) to help individuals scan their iPhone and Android devices for evidence of compromise.
Besides making use of social engineering tricks by designing a rogue website with an identical look and feel of Amnesty International’s legitimate portal, the modus operandi aims to trick the visitor into downloading an “Amnesty Anti Pegasus Software” under the guise of an antivirus tool that features capabilities to enable the bad actor find way a remote way into the compromised machine and exfiltrate sensitive information, such as login credentials.
The Sarwent sample used in the low-volume campaign is a highly-customized variant coded in Delphi and is capable of allowing remote desktop access through VNC or RDP and executing command line or PowerShell instructions received from an attacker-controlled domain, the results of which are sent back to the server.
Talos attributed the infections with high confidence to a Russian-speaking actor locating in the country and known for mounting attacks involving the Sarwent backdoor since at least January 2021 sprawling across a variety of victims, noting the level of modifications made to the supposed antivirus as likely evidence that “the operator has access to the source code of the Sarwent malware.”
“The campaign targets people who might be concerned that they are targeted by the Pegasus spyware,” the researchers said. “This targeting raises issues of possible state involvement, but there is insufficient information […] to make any determination on which state or nation. It is possible that this is simply a financially motivated actor looking to leverage headlines to gain new access.”